Nomad
June 23, 2024, 3:48pm
1
Hi,
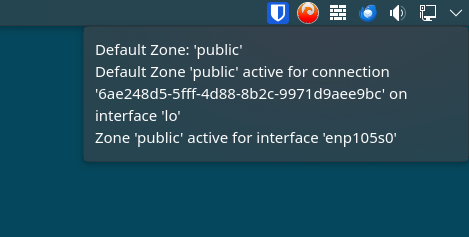
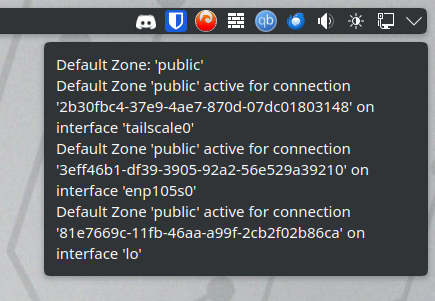
I decided to download the firewall-applet on my Debian system and when I hover my cursor over the system tray icon I get different results as you can see in the screenshots below. Both of my systems have the exact same network settings, for example, being connected to tailscale.
That being said, I have a few questions.
#1 . Does firewall-applet ship in EOS pre-configured? If no, why does it have different settings than when freshly installed on Debian?
#2 . If the answer to the first question is yes, would I just need to copy the config folder for firewall-applet to my Debian system to have the same settings, and is that even a good idea since they’re different systems?
#3 . I’ve never actually configured any settings in firewall-applet before. Should I be, or is it a download it and forget it type applet?
EOS
Debian
dalto
June 23, 2024, 3:52pm
2
The applet just shows you what is configured in firewalld
It looks like the EOS one is showing your tailscale connection.
firewalld usually comes preconfigured with sane defaults. I have never used it on debian but I would hope it would be the same there.
I don’t use either EOS or Debian and I don’t use the firewall applet, but my first question would be do the lo and tailescale interface show up when you run ip a in a terminal? If so I would check somewhere in the setting of the firewall-applet settings, maybe there is a setting you have to check to display none default interfaces in the nm-applet?
Nomad
June 23, 2024, 3:54pm
4
Correct, but why wouldn’t the Debian one show the same? Both systems are exactly the same in terms of network settings.
dalto
June 23, 2024, 3:56pm
5
Try running nmcli con show in both systems.
Nomad
June 23, 2024, 3:59pm
6
user@Debian:~$ nmcli con show
NAME UUID TYPE DEVICE
Wired connection 1 4ac4a8c0-1160-4434-8ff4-deda224459f8 ethernet enp105s0
tailscale0 21718cf2-c7b0-4da0-9f0d-f3ff9c18ab7f tun tailscale0
lo 6ae248d5-5fff-4d88-8b2c-9971d9aee9bc loopback lo
Debian
EOS
[user@EOS ~]$ nmcli con show
NAME UUID TYPE DEVICE
Wired connection 1 3eff46b1-df39-3905-92a2-56e529a39210 ethernet enp105s0
tailscale0 2b30fbc4-37e9-4ae7-870d-07dc01803148 tun tailscale0
lo 81e7669c-11fb-46aa-a99f-2cb2f02b86ca loopback lo
Nomad
June 23, 2024, 4:00pm
7
Edit: Yes they both show it.
dalto
June 23, 2024, 4:01pm
8
Were you connected to tailscale on both when you took those initial screenshots?
Nomad
June 23, 2024, 4:01pm
9
Yes. Always connected to tailscale.
What settings options do you have when you open the firewall-applet interface, is there a interfaces section there?
dalto
June 23, 2024, 4:02pm
11
That is the only difference. Debian isn’t showing tailscale. Perhaps your tailscale setup differs in some way?
dalto
June 23, 2024, 4:03pm
12
It is just shows the state of firewalld. The interfaces and connections are all coming from network manager.
Nomad
June 23, 2024, 4:03pm
13
I’m not sure. Both are connected and both were set up using tailscale’s website’s instructions specifically for both Debian and Arch.
Ah yeah I forgot about that, it’s just a gui/frontend for what you would normally see with firewall-cmd command. Thanks for reminding me!
Nomad
June 23, 2024, 4:07pm
15
Should I just leave the firewall-applet on Debian alone, or is there any reason to copy my EOS config file over to it?
What do you see on both systems when you run firewall-cmd --list-all-zones?
Nomad
June 23, 2024, 4:16pm
17
user@Debian:~$ firewall-cmd --list-all-zones
block
target: %%REJECT%%
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
dmz
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
drop
target: DROP
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
external
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
forward: yes
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
home
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
internal
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
nm-shared
target: ACCEPT
icmp-block-inversion: no
interfaces:
sources:
services: dhcp dns ssh
ports:
protocols: icmp ipv6-icmp
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule priority="32767" reject
public (active)
target: default
icmp-block-inversion: no
interfaces: enp105s0
sources:
services: dhcpv6-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
trusted
target: ACCEPT
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
work
target: default
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
Debian
EOS
[user@Arch ~]$ firewall-cmd --list-all-zones
block
target: %%REJECT%%
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
dmz
target: default
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
drop
target: DROP
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
external
target: default
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
forward: yes
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
home
target: default
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
internal
target: default
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
nm-shared
target: ACCEPT
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services: dhcp dns ssh
ports:
protocols: icmp ipv6-icmp
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule priority="32767" reject
public (default, active)
target: default
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces: enp105s0
sources:
services: dhcpv6-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
trusted
target: ACCEPT
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
work
target: default
ingress-priority: 0
egress-priority: 0
icmp-block-inversion: no
interfaces:
sources:
services: dhcpv6-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
I kind of expected those other interfaces listed there but it seems in my Debian vm the one I thought that would be listed is not listed, so I was wrong in my thinking direction. Will try and install KDE Plasma on my Debian vm to see if I can come up with something.
1 Like
What version of KDE Plasma did you install?
kde-full
kde-standard
kde-plasma-desktop
task-kde-desktop
![]()
![]()