Hi guys,
I have been looking the forum about fire wall and securing my system.
I came across several posts talking about installing different firewalls but I came across this interesting post by our friend @dalto FirewallD on Apollo ISO - #11 by dalto that had a link to https://discovery.endeavouros.com/applications/firewalld/2022/03/
Reading this page I conclude that it is already done by the wonderfull developers and no need to bother with trying any other firewall.
As my rule of thumb I always prefer to stick to the defaults, so there is no need to try or attempt anything else.
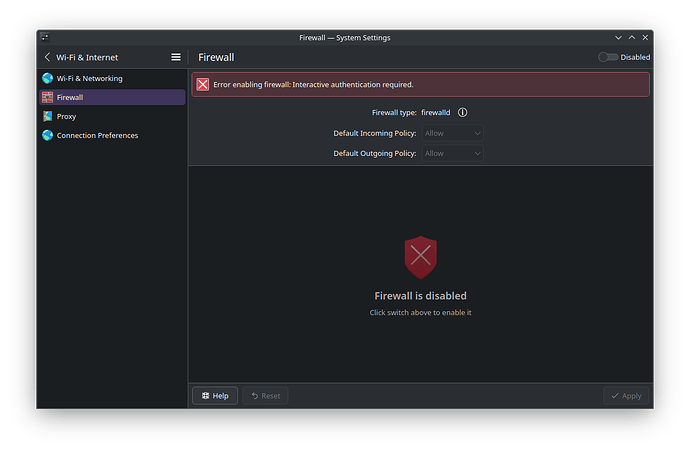
As far as I understand, it is just installed but not configured or active and I should manually configure it to be effective.
My question is did I get it correct?
Is there any “default” setting perhaps instead of playing with it and mess things up?
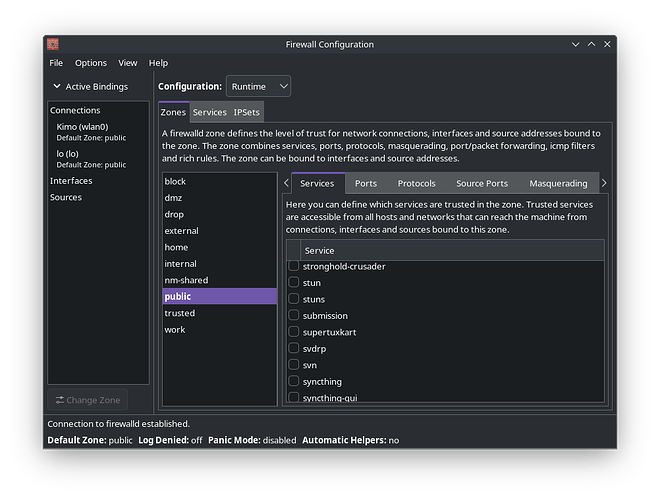
I see 2 apps, one saying control your network rules and the other saying Firewall configuration.
Honestly I never thought of attended to firewalls before that and I do not know what is this and what s that?
Which one to start with, what to do and what not to do.
As any home user, I am browsing the web, downloading some stuff (PDFs and books mainly), and I am using Brave browser. Sometimes I use torrents to download some other distros to play with on some old laptops I have.
As firewall is for me a serious business and Ido not want to be locked out or having an app that needs the internet like pCloud or similar, or VLC sometimes need internet, so I do not want to lock my self out. (again I am not that techie, and never bothered with firewall)
I won;t need anything other than firewalld to have a good firewall? Will it automatically make all ports stealth or I need to do it manually?
Any hints or guidance will be highly appreciated as I said I see it a serious business and I do not want to ignorantly do something that locks me out or disable something I need.
Thank you in advance for your hints and guidance.
Edit: Reading about firewalls and searching I cam across some suggestions somewhere suggesting to use nftables instead. Honestly as for now I do not know what is the difference from firewalld. I will appreciate hints about it as well.