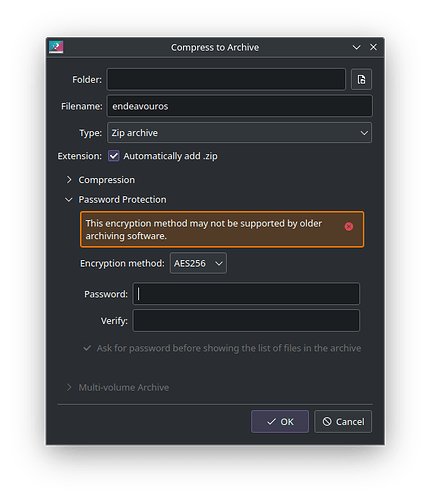
Hi friends. When I was using Windows, I used 7-zip to securely password-zip my files with AES 256 in 7z format.
I abandoned Windows and now only use EOS KDE. I found that the only way to compress with a password was to use the ZIP format that KDE’s ARK brings, since the other formats do not allow me to compress with a password. I also installed p7zip and it can be used from ARK, and this one also allows me to use password.
I would like to know the following things, if possible:
-
Is ARK ZIP (default) with AES 256 password, or P7ZIP (.7z) with AES 256 password more secure?
-
Does a maximally compressed file with a password become more secure than an uncompressed file with a password?
-
I have heard that some “7-zip” in the ARCH and AUR repository (and in most repositories) are versions made by third parties, or closed source, or that they are outdated. Also, some of these versions should not be used because they do not save some user permissions in Linux (I don’t know what this is, but it worries me and I would like to avoid these versions if possible, since I have read many people saying this on reddit and other forums).
-
If ZIP is better than 7Z, there is no problem because I already have it installed, and I will continue using it. But if you confirm that 7Z is better, which one should I install? Many appear in the ARCH repository, and many more appear in the AUR repository. Some with the “file manager” tag and others with the “file compressor” tag. I don’t know which one works with Linux permissions, it is free source and up to date.
-
Is there a more secure method to compress files with a password? AES 256 is the best known I think, but I would like to know if there is something more secure for compressing files, although I think this is the best known. I’m looking for something with a GUI since I use the terminal for everything else, but creating files and compressing files I prefer a GUI like ARK’s (or similar, in case you tell me there is something better).
Sorry for so much text, and thanks in advance for your time and help, friends.