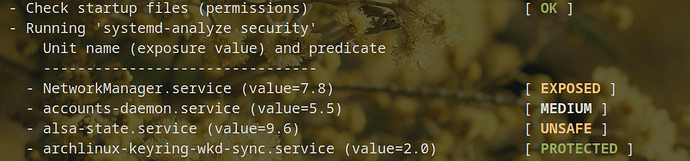
I just finished hardening all my systemd services that were rated as “exposed” or “unsafe”; now they are all “medium” or “OK”.
❯ systemd-analyze security
UNIT EXPOSURE PREDICATE HAPPY
NetworkManager.service 4.2 OK 🙂
archlinux-keyring-wkd-sync.service 2.0 OK 🙂
bluetooth.service 6.0 MEDIUM 😐
dbus-broker.service 4.2 OK 🙂
dirmngr@etc-pacman.d-gnupg.service 3.7 OK 🙂
dm-event.service 3.8 OK 🙂
emergency.service 3.8 OK 🙂
firewalld.service 7.3 MEDIUM 😐
getty@tty1.service 4.1 OK 🙂
gpg-agent@etc-pacman.d-gnupg.service 3.7 OK 🙂
greetd.service 7.1 MEDIUM 😐
keyboxd@etc-pacman.d-gnupg.service 3.7 OK 🙂
polkit.service 1.2 OK 🙂
rescue.service 2.2 OK 🙂
rtkit-daemon.service 3.5 OK 🙂
shadow.service 1.2 OK 🙂
snapper-cleanup.service 6.7 MEDIUM 😐
systemd-ask-password-console.service 1.0 OK 🙂
systemd-ask-password-wall.service 1.3 OK 🙂
systemd-bsod.service 3.8 OK 🙂
systemd-hostnamed.service 1.7 OK 🙂
systemd-importd.service 5.0 MEDIUM 😐
systemd-journald.service 4.9 OK 🙂
systemd-logind.service 2.8 OK 🙂
systemd-oomd.service 1.8 OK 🙂
systemd-rfkill.service 1.0 OK 🙂
systemd-udevd.service 7.0 MEDIUM 😐
systemd-userdbd.service 2.3 OK 🙂
tuned-ppd.service 1.8 OK 🙂
tuned.service 1.8 OK 🙂
upower.service 2.4 OK 🙂
user@1000.service 5.1 MEDIUM 😐
whoogle.service 3.3 OK 🙂
wpa_supplicant.service 3.0 OK 🙂
Except for greetd.service and user@.service (which I did make an effort to harden–that’s as far as I could get them without breaking stuff), the “medium” ones I haven’t hardened yet. I may double back and do those, but it’s not going to keep me up at night if I don’t get around to it.
Just to go ahead and say the quiet part out loud: hardening my systemd services is way beyond what I consider necessary for my personal threat model. That’s not to say it is pointless, or people shouldn’t do it, or anything like that…just for me personally, it seems a bit overkill.
It’s also kind of hard! It’s not always obvious what a service should or should not have access to. In a lot of cases I had to double-back and bisect the drop-in because I added something that was breaking the service and I wasn’t sure what. I had to mount the disk from a live ISO a couple times because I broke something and couldn’t get back in (be careful when you harden the dbus-broker service!  ).
).
It has been an interesting little project though! I have learned a lot while doing it.
Getting rid of all the “exposed” and “unsafe” ratings did boost the Lynis score by a whopping two points. It seems a bit stingy given how time consuming it ended up being! 
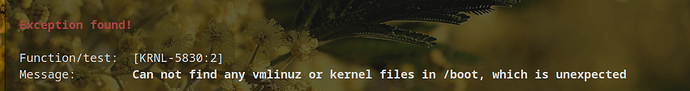
But honestly the Lynis score should not be taken too seriously in my opinion. For example:
-[ Lynis 3.1.4 Results ]-
Warnings (3):
----------------------------
! Reboot of system is most likely needed [KRNL-5830]
- Solution : reboot
https://cisofy.com/lynis/controls/KRNL-5830/
I always get this reboot warning, even if I reboot and run the audit immediately after logging in. Just me?
Also, while a lot of the Lynis suggestions are good and interesting and worthy of research, some of them just seem like they don’t really matter. Like “add a legal banner to /etc/issue, to warn unauthorized users.” I guess I could do that, but it really doesn’t seem like it will make my computer more secure.
One of the suggestions was to install a malware scanner and it listed a couple suggestions. Out of the suggestions I picked rkhunter because it’s in the extra repo and from the ArchWiki article it looked like it was easy to get started. I ran the thing, it didn’t find any rootkits which is good I guess, but the fact that the output has one thousand grep syntax warnings was puzzling. So I took a closer look at the project and discovered it hasn’t had a stable release since 2018. http://rkhunter.sourceforge.net/
Maybe that doesn’t say much for me that I installed that on my computer, but I feel like it really doesn’t say much for Lynis which happily added a point to my score. “Yep, I see you have Rootkit Hunter on there, good job, your computer is safer now.” Is it? It’s probably more of a vulnerability than anything to have this ancient software on here, searching for rootkits that were relevant in 2018.
Anyway, all that to say: I like Lynis, I think the information is generally good and useful, but it ought to be taken with a grain of salt because how relevant it is will vary a good deal from person to person.