Hey everyone,
Not sure if this is the section to post this so let me know if I should move it. I’m curious if anyone knows if fwupd would still be safe to use after the whole MSI leak. I use fwupd to update my firmware and after the threat actors started to release all of the information that they had - articles have said to install updates from the MSI website directly as well as the hacker group having signing keys. Well, we’re on Linux so we don’t just go and download an .exe file like they do on Windows. My firmware has updates to be had, I am just reluctant to update them with fwupd.
Does anyone have advice on this?
I appreciate it
you can check on site MSI for your motherboard ,
see also
https://fwupd.org/lvfs/vendors/#msi
inxi -Fza will help you
1 Like
Ive never used fwupd on linux but i have lots of MSI product. I update mine from the MSI website. Check if there is a newer version. Download the newer version and then extract the files and copy the folder containing the newer files to a usb. Then boot into your UEFI firmware (Bios) and use the flash tool provided in the the UEFI settings screen called M-Flash. Select the newer update from the folder on the usb. Make sure your system is plugged in when updating your UEFI Firmware (Bios)
Edit: I am doing one right now as i see there is an update for mine.
1 Like
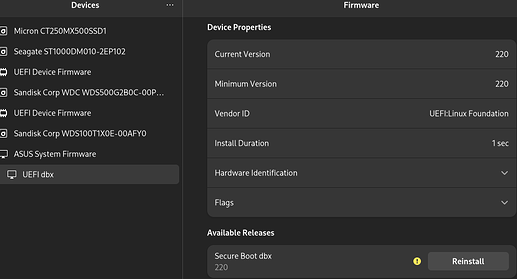
I decided to check firmware updates here and all I got was secure boot dbx keys, which I don’t need to update because I’m not using secure boot. But this is a nice tool…
Ive actually never used the fwupdate tool. I’m so used to doing it directly either downloading the file or it can be done directly online also. Or there is the Windows way. 
Edit: I just never see any listing for MSI on the site.
Edit2: The update i just did was for:
Description:
- AGESA ComboAm4v2PI 1.2.0.A. update.
- TPM Out of Bounds Access security patch.
This is the only thing that showed with an update available.
I did update from 217 to 220 to see if it would work and it worked…
It seems that this update mitigates boothole vulnerability by updating the keys (removing compromised keys) from secure boot dbx…
All other devices are up to date, but this is a nice tool to have, to check updates from time to time…
How do you run it? Just fwupdate or do you need sudo?
I downloaded gnome-firmware utility, which installs fwupd.
But you don’t need a GUI utility…
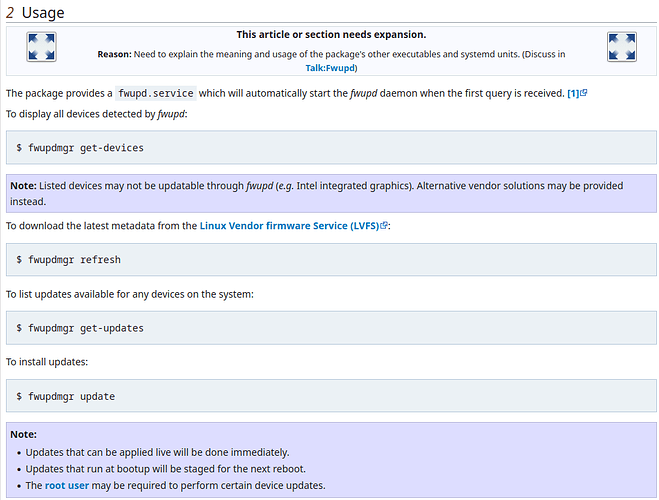
You could just follow this guide.
Edit:
KDE has a utility for it, you could check if it fits your needs…
1 Like
Yes, Thanks!
I just tried it and it did update for those unlisted keys or whatever. I had already updated the firmware from MSI. I kind of wished i had tried this first to see if it had the latest BIOS version that i just updated to.
These dbx key updates are not permanent… I did some tests…
I’m not sure if this happens to all motherboards, but here, in Asus B550-F, I went to UEFI and cleared my secure boot keys after the update gnome-firmware update.
Boot again, then, in UEFI, restored the factory default keys to secure boot.
Gnome-firmware showed the updates again… So, in my point of view, these dbx updates are safe to do, but not really necessary since we are not using secure boot with EnOS…
I agree with you. As far as i know the keys on my MSI boards get automatically installed when you enable secure boot and you can clear them or use custom keys. They must get downloaded from the MSI site i assume with the firmware.
1 Like