Today I thought I’d have a play around with firewalld, specifically geoblocking.
I downloaded a a range of addresses…
cd Downloads
wget http://www.ipdeny.com/ipblocks/data/countries/all-zones.tar.gz
tar -vxzf all-zones.tar.gz
I created a new IP set called blacklist from the Firewall Applet and attempted to add entried from file. Unforunately this just causes the filewall process to ramp up to 100% and after 15 minutes I decided to kill the process.
Assuming this to be a bug I decided to add the files manually using…
firewall-cmd --permanent --ipset=blacklist --add-entries-from-file=./cn.zone
firewall-cmd --permanent --ipset=blacklist --add-entries-from-file=./ru.zone
This worked pretty much instantly.
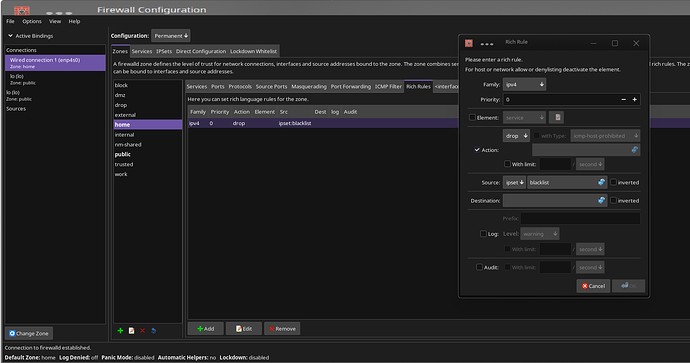
Now I wanted to create a rich rule in my ‘home’ zone that would drop anything in the ipset called blacklist so I used…
Sudo firewall-cmd --permanent --zone=home --add-rich-rule='rule source ipset=blacklist drop'
sudo firewall-cmd –reload
sudo systemctl restart firewalld
To test this I used www.chinadaily.com.cn
The browser was able to access it still!
dig www.chinadaily.com.cn +short
79.133.176.226
79.133.176.227
79.133.176.228
79.133.176.229
79.133.176.230
79.133.176.231
79.133.176.224
79.133.176.225
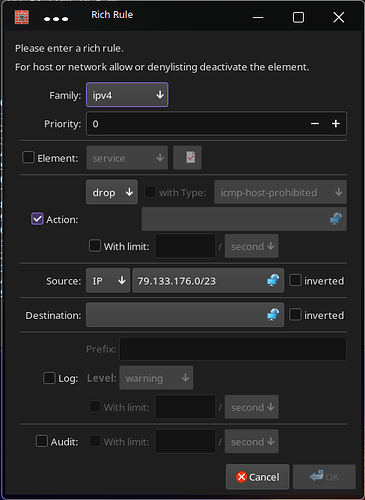
I looked in the ipset called blacklist to see if the range was covered and it does have the entry 79.133.176.0/23 which covers the range mentioned above.
I stil get a ping response.
I can also still access the website.
So I checked the active zones which look good…
sudo firewall-cmd --get-active-zones
home
interfaces: enp4s0
sources: ipset:blacklist
sudo firewall-cmd --zone=home --list-all
home (active)
target: default
icmp-block-inversion: no
interfaces: enp4s0
sources: ipset:blacklist
services: dhcpv6-client mdns samba-client ssh
ports:
protocols:
forward: yes
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule source ipset=“blacklist” drop
This is very strange. Not sure what I’ve done wrong so if anyone has any ideas please shout em my way :-).