My experience with 3 computers to move from mkinitcpio to dracut: 2 laptop and 1 desktop PC were total failure. I’m using LUKS-encrypted partitions on all computers, that encryption is offered during EndeavourOS installation via Calamares (LUKS1 is used as GRUB2 still does not support properly LUKS2, although cryptsetup is using LUKS2 by default). On those machines were root partition (EXT4, encrypted) together with boot folder but EFI (512 MiB FAT32, ~10 MiB used, unencrypted) and home (EXT4, encrypted) are separate partitions.
First result when using guidance at here, was one unbootable desktop PC remotely, which still is waiting to be fixed.
What is wrong with that tutorial? First place: how to properly move back from dracut to mkinitcpio is currently missing.
Initially after dracut was installed, reconfigure-kernels command started, still I ended up after reboot in unbootable system. I somehow needed also reinstall GRUB via chroot:
sudo grub-install --target=x86_64-efi --efi-directory=/boot/efi --bootloader-id=EndeavourOS-grub --modules="part_gpt part_msdos"
sudo grub-mkconfig -o /boot/grub/grub.cfg
These additional modules were needed due to LUKS-encrypted partitions. Without these modules there were some error messages during boot but still booted. With these modules these error messages are gone.
When you are using LUKS-encrypted partitions, entering to chroot is a bit more challenging:
lsblk -f # this will show proper UUID value of encrypted partition, also after decrypting it is useful to check again with that command
sudo cryptsetup open --type luks --allow-discards /dev/nvme0n1p2 mycryptdevice && sudo mkdir -p /run/media/liveuser/<UUID> && sudo mount /dev/mapper/mycryptdevice /run/media/liveuser/<UUID> && sudo arch-chroot /run/media/liveuser/<UUID> && sudo mount /dev/nvme0n1p1 /boot/efi
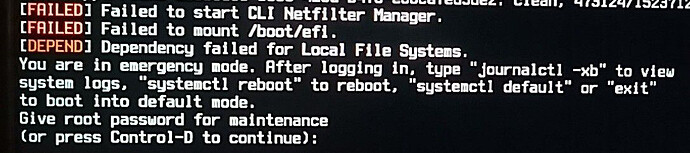
There is needed to fine tune the dracut conf - this does not work out of the box in case LUKS-encrypted partitions. I got error messages: “EFI mount failed, Failed to start CLI Netfilter Manager”
Then tried to figure out, what is needed to add to dracut conf. First checked logs:
journalctl -xb -p err
Failed to start CLI Netfilter Manager.
A start job for unit ufw.service has failed
Failed to mount /boot/efi.
A start job for unit boot-efi.mount has failed
Then investigated:
journalctl --boot=-1 --unit=ufw.service
ufw.service: Main process exited, code=exited, status=1/FAILURE
ufw.service: Failed with result 'exit-code'.
ufw-init[381]: modprobe: FATAL: Module ip_tables not found in directory /lib/modules/6.1.3-arch1-1
find /lib/modules/ -type f -iname "*ip_tables*"
./6.1.4-arch1-1/build/include/uapi/linux/netfilter_ipv4/ip_tables.h
./6.1.4-arch1-1/build/include/linux/netfilter_ipv4/ip_tables.h
./6.1.4-arch1-1/kernel/net/ipv4/netfilter/ip_tables.ko.zst
journalctl --boot=-1 --unit=boot-efi.mount
mount: /boot/efi: unknown filesystem type 'vfat'.
boot-efi.mount: Mount process exited, code=exited, status=32/n/a
boot-efi.mount: Failed with result 'exit-code'.
Somehow it searched module from wrong folder - this shows, that initramfs was not properly updated. There were kernel update from 6.1.3 to 6.1.4 happened beforehand.
Then tried to load vfat module via dracut.
Firstly checked, which modules exist:
find /lib/modules/6.1.4-arch1-1/kernel -type f -iname "*fat*"
./fs/fat/fat.ko.zst
./fs/fat/vfat.ko.zst
./fs/exfat/exfat.ko.zst
Then read dracut official guidance and created a file /etc/dracut.conf.d/filesystems.conf with content:
filesystems+=" vfat "
Then regenerated initramfs:
sudo reinstall-kernels 1>reinstall.log 2>reinstall-error.log
This was intentional to get full logs.
Crucial parts from log:
dracut-install: Failed to find module 'vfat '
dracut: FAILED: /usr/lib/dracut/dracut-install -D /var/tmp/dracut.5FI5Dy/initramfs --kerneldir /lib/modules/6.1.4-arch1-1/ -m vfat
We remember, that previously we checked, that vfat module existed at /lib/modules/6.1.4-arch1-1/kernel/fs/fat/vfat.ko.zst and also /lib/modules/6.1.4-arch1-1/kernel/fs/fat/fat.ko.zst were there.
Here are full logs:
reinstall-kernels-logs.pdf (79.0 KB)
Just to mention, that packages kernel-install-for-dracut binutils elfutils pigz were installed while moved from mkinitcpio to dracut.
Then I decided to move back to mkinitcpio from dracut:
sudo pacman -Syu mkinitcpio # agree with kernel-install-for-dracut removal
sudo pacman -Rns dracut cpio elfutils pigz
… as these packages were installed and now not needed. Also /var/log/pacman.log confirmed, what were installed, although I documented initially, when installed dracut, which packages were installed and which removed:
[2023-01-05T20:46:55+0200] [PACMAN] Running 'pacman -Syu --needed kernel-install-for-dracut'
[2023-01-05T20:46:55+0200] [PACMAN] synchronizing package lists
[2023-01-05T20:46:56+0200] [PACMAN] starting full system upgrade
[2023-01-05T20:49:27+0200] [PACMAN] Running 'pacman -Rns mkinitcpio-openswap'
[2023-01-05T20:49:32+0200] [ALPM] transaction started
[2023-01-05T20:49:32+0200] [ALPM] removed mkinitcpio-openswap (0.1.0-3)
[2023-01-05T20:49:32+0200] [ALPM] transaction completed
[2023-01-05T20:49:32+0200] [ALPM] running '30-systemd-update.hook'...
[2023-01-05T20:49:36+0200] [PACMAN] Running 'pacman -Syu --needed kernel-install-for-dracut'
[2023-01-05T20:49:36+0200] [PACMAN] synchronizing package lists
[2023-01-05T20:49:36+0200] [PACMAN] starting full system upgrade
[2023-01-05T20:49:46+0200] [ALPM] running '60-mkinitcpio-remove.hook'...
[2023-01-05T20:49:46+0200] [ALPM] transaction started
[2023-01-05T20:49:46+0200] [ALPM] warning: /etc/mkinitcpio.conf saved as /etc/mkinitcpio.conf.pacsave
[2023-01-05T20:49:46+0200] [ALPM] removed mkinitcpio (34-2)
[2023-01-05T20:49:46+0200] [ALPM] installed cpio (2.13-3)
[2023-01-05T20:49:46+0200] [ALPM] installed dracut (056-1)
[2023-01-05T20:49:46+0200] [ALPM] installed kernel-install-for-dracut (1.6-1)
Yes, we needed to remove mkinitcpio-openswap initially in order to install kernel-install-for-dracut and its dependencies as guided also here.
Then rebuilt kernel in chroot environment again.
sudo pacman -Syu mkinitcpio-openswap
This may vary as sometimes you might need to reinstall even kernel itself (sudo pacman -Syu linux).
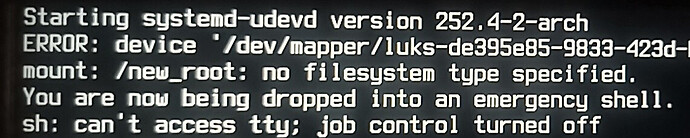
Result was emergency shell:
Then finally discovered, what was wrong. Thanks to hints from EndeavourOS IRC there was found, that /etc/mkinitcpio.conf file was changed, missing parts were:
FILES="/crypto_keyfile.bin"
HOOKS="base udev autodetect modconf block keyboard keymap encrypt filesystems fsck"
COMPRESSION="zstd"
Then restored it:
sudo cp /etc/mkinitcpio.conf.pacsave /etc/mkinitcpio.conf
Then updated initramfs via reinstalling:
yay -S mkinitcpio-openswap
If you are in chroot environment, then often is live USB kernel version different than in chrooted OS. Therefore you cannot even use mkinitcpio -P. Actually inside /etc/mkinitcpio.d/ folder were no profiles, so that command did not work anyway.
Then finally after exiting chroot and rebooting from local storage, I got back the system.
Conclusion: I guess dracut is good system but for LUKS1, LUKS2-encrypted partitions there is needed to improve it. Also guidance and official announcement - I was impressed by decision, that dracut was officially adopted in EndeavourOS 2022.12 Cassini and therefore decided also to move to it but it was too early.