As per my initial post
Thanks for that idea! I have set the do not automount attribute on my drive but it didn’t resolve the problem unfortunately.
Here are all the files and info you asked for:
gdisk info for the drive and partition
Command (? for help): p
Disk /dev/sdc: 1953525168 sectors, 931.5 GiB
Model: WDC WD10EZEX-08W
Sector size (logical/physical): 512/4096 bytes
Disk identifier (GUID): F184E901-ED8F-4AF1-9DC5-8EF1F0D04862
Partition table holds up to 128 entries
Main partition table begins at sector 2 and ends at sector 33
First usable sector is 34, last usable sector is 1953525134
Partitions will be aligned on 2048-sector boundaries
Total free space is 2014 sectors (1007.0 KiB)
Number Start (sector) End (sector) Size Code Name
1 2048 1953525134 931.5 GiB 8300
Command (? for help): i
Using 1
Partition GUID code: 0FC63DAF-8483-4772-8E79-3D69D8477DE4 (Linux filesystem)
Partition unique GUID: F2BF64D3-B018-4D82-9D13-82BCE8EF92D3
First sector: 2048 (at 1024.0 KiB)
Last sector: 1953525134 (at 931.5 GiB)
Partition size: 1953523087 sectors (931.5 GiB)
Attribute flags: 8000000000000000
Partition name: ''
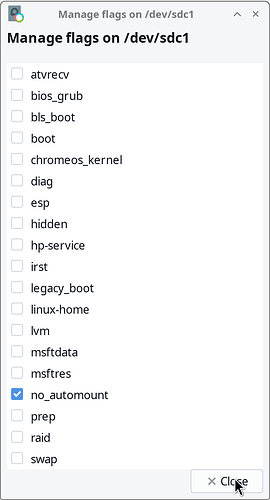
gparted screenshot of flags
/etc/fstab
cat /etc/fstab
# /etc/fstab: static file system information.
#
# Use 'blkid' to print the universally unique identifier for a device; this may
# be used with UUID= as a more robust way to name devices that works even if
# disks are added and removed. See fstab(5).
#
# <file system> <mount point> <type> <options> <dump> <pass>
UUID=8901-DC4B /efi vfat umask=0077 0 2
/dev/mapper/luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 / ext4 defaults,noatime 0 1
tmpfs /tmp tmpfs defaults,noatime,mode=1777 0 0
For completeness sake, the first file system that’s listed here refers to sda1 not sdc1 the “drive b” I’m talking about.
ls -l /dev/disk/by-uuid/8901-DC4B
lrwxrwxrwx 1 root root 10 Sep 14 11:44 /dev/disk/by-uuid/8901-DC4B -> ../../sda1
/etc/crypttab
cat /etc/crypttab
# /etc/crypttab: mappings for encrypted partitions.
#
# Each mapped device will be created in /dev/mapper, so your /etc/fstab
# should use the /dev/mapper/<name> paths for encrypted devices.
#
# See crypttab(5) for the supported syntax.
#
# NOTE: Do not list your root (/) partition here, it must be set up
# beforehand by the initramfs (/etc/mkinitcpio.conf). The same applies
# to encrypted swap, which should be set up with mkinitcpio-openswap
# for resume support.
#
# <name> <device> <password> <options>
luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 UUID=28ded036-cbcc-4ea1-b4e1-25a9555de0f2 /crypto_keyfile.bin luks
/proc/cmdline
cat /proc/cmdline
initrd=\600f0b1a47f14a08a960d8b4e97ac812\6.10.9-arch1-2\initrd root=UUID=a9cd9832-fa2d-4f16-998d-29b64fbf604a rw quiet cryptdevice=UUID=28ded036-cbcc-4ea1-b4e1-25a9555de0f2:luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 root=/dev/mapper/luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 loglevel=3 nowatchdog systemd.machine_id=600f0b1a47f14a08a960d8b4e97ac812
/etc/kernel/cmdline
cat /etc/kernel/cmdline
root=UUID=a9cd9832-fa2d-4f16-998d-29b64fbf604a rw quiet cryptdevice=UUID=28ded036-cbcc-4ea1-b4e1-25a9555de0f2:luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 root=/dev/mapper/luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 loglevel=3 nowatchdog
lsblk
lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS
sda 8:0 0 232.9G 0 disk
├─sda1 8:1 0 512M 0 part /efi
└─sda2 8:2 0 232.4G 0 part
└─luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2 254:0 0 232.4G 0 crypt /
sdb 8:16 0 596.2G 0 disk
└─sdb1 8:17 0 596.2G 0 part
sdc 8:32 0 931.5G 0 disk
└─sdc1 8:33 0 931.5G 0 part
sr0 11:0 1 1024M 0 rom
nvme0n1 259:0 0 232.9G 0 disk
├─nvme0n1p1 259:1 0 539M 0 part
├─nvme0n1p2 259:2 0 500M 0 part
├─nvme0n1p3 259:3 0 231.1G 0 part
└─nvme0n1p4 259:4 0 762M 0 part
blkid
blkid
/dev/nvme0n1p3: BLOCK_SIZE="512" UUID="36C82BDDC82B99DF" TYPE="ntfs" PARTUUID="bc3590c8-22bc-11ed-8ce1-782b46d95edf"
/dev/nvme0n1p1: BLOCK_SIZE="512" UUID="680C8BF00C8BB798" TYPE="ntfs" PARTUUID="bc3590c6-22bc-11ed-8ce1-782b46d95edf"
/dev/nvme0n1p4: BLOCK_SIZE="512" UUID="803C003A3C002DAA" TYPE="ntfs" PARTUUID="a5f76424-a933-44b2-8355-1eb5efa85120"
/dev/nvme0n1p2: UUID="5A10-59F6" BLOCK_SIZE="512" TYPE="vfat" PARTUUID="bc3590c7-22bc-11ed-8ce1-782b46d95edf"
/dev/sdb1: BLOCK_SIZE="512" UUID="7876B2A75AA3E12D" TYPE="ntfs" PARTUUID="157747ad-01"
/dev/mapper/luks-28ded036-cbcc-4ea1-b4e1-25a9555de0f2: UUID="a9cd9832-fa2d-4f16-998d-29b64fbf604a" BLOCK_SIZE="4096" TYPE="ext4"
/dev/sdc1: UUID="6ed8cf7b-1fb2-4dad-9648-14adb275e8f7" TYPE="crypto_LUKS" PARTUUID="f2bf64d3-b018-4d82-9d13-82bce8ef92d3"
/dev/sda2: UUID="28ded036-cbcc-4ea1-b4e1-25a9555de0f2" TYPE="crypto_LUKS" PARTUUID="b1d3b8a3-125e-9f4c-b624-e0db7e84c4be"
/dev/sda1: LABEL_FATBOOT="NO_LABEL" LABEL="NO_LABEL" UUID="8901-DC4B" BLOCK_SIZE="512" TYPE="vfat" PARTUUID="a3a8eadc-e266-aa48-be08-d393c88cc8d4"
I have also tried running systemd-cryptsetup-generator with an empty folder as first parameter to see the files it generates. It doesn’t generate a file for drive b and thus seems to operate correctly. Nonetheless, I always end up with a systemd unit without a unit file for drive b after I reboot. 
systemctl status systemd-cryptsetup@luks\\x2d6ed8cf7b\\x2d1fb2\\x2d4dad\\x2d9648\\x2d14adb275e8f7.service
× systemd-cryptsetup@luks\x2d6ed8cf7b\x2d1fb2\x2d4dad\x2d9648\x2d14adb275e8f7.service
Loaded: not-found (Reason: Unit systemd-cryptsetup@luks\x2d6ed8cf7b\x2d1fb2\x2d4dad\x2d9648\x2d14adb275e8f7.service not found.)
Active: failed (Result: exit-code) since Sat 2024-09-14 11:44:36 CEST; 24min ago
Invocation: 52415f836dd04834951ded7d418f129f
Main PID: 529 (code=exited, status=1/FAILURE)
Mem peak: 1G
CPU: 19.952s
Sep 14 11:44:30 val systemd-cryptsetup[529]: Failed to activate with specified passphrase. (Passphrase incorrect?)
Sep 14 11:44:32 val systemd-cryptsetup[529]: Set cipher aes, mode xts-plain64, key size 256 bits for device /dev/sdc1.
Sep 14 11:44:34 val systemd-cryptsetup[529]: Failed to activate with specified passphrase. (Passphrase incorrect?)
Sep 14 11:44:34 val systemd-cryptsetup[529]: Set cipher aes, mode xts-plain64, key size 256 bits for device /dev/sdc1.
Sep 14 11:44:36 val systemd-cryptsetup[529]: Failed to activate with specified passphrase. (Passphrase incorrect?)
Sep 14 11:44:36 val systemd-cryptsetup[529]: Too many attempts to activate; giving up.
Sep 14 11:44:36 val systemd[1]: systemd-cryptsetup@luks\x2d6ed8cf7b\x2d1fb2\x2d4dad\x2d9648\x2d14adb275e8f7.service: Main process exited, code=exited, status=1/>
Sep 14 11:44:36 val systemd[1]: systemd-cryptsetup@luks\x2d6ed8cf7b\x2d1fb2\x2d4dad\x2d9648\x2d14adb275e8f7.service: Failed with result 'exit-code'.
Sep 14 11:44:36 val systemd[1]: Failed to start Cryptography Setup for luks-6ed8cf7b-1fb2-4dad-9648-14adb275e8f7.
Sep 14 11:44:36 val systemd[1]: systemd-cryptsetup@luks\x2d6ed8cf7b\x2d1fb2\x2d4dad\x2d9648\x2d14adb275e8f7.service: Consumed 19.952s CPU time, 1G memory peak.