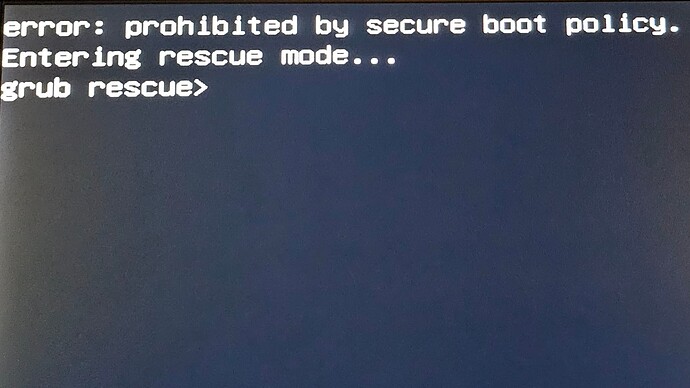
Hey, I’ve enabled grub secure boot support by deleting the previous keys and signing the new ones using sbctl, sbctl verify verified that all needed file are signed but I still get this error:
Not sure if anyone here use’s secure boot. There is this from the arch wiki
https://wiki.archlinux.org/title/GRUB#Secure_Boot_support
I’ve read the wiki along with a few other guides, and I’ve figured out how to set it up. I’ll explain the process in case anyone else needs it. ![]()
First, you need to put your system into “Setup Mode” by deleting the old signed keys in your BIOS. On my MSI motherboard, this was found under: Settings → Advanced → Windows OS Configuration → Secure Boot. Keep Secure Boot disabled but set it to Custom mode so you can delete the old keys.
After deleting the keys, boot back into EndeavourOS. Next, install sbctl using sudo pacman -Sy sbctl and reinstall GRUB with the following command:
sudo grub-install --target=x86_64-efi --efi-directory=esp --bootloader-id=GRUB --modules="tpm" --disable-shim-lock
In this command, replace esp with your boot partition. In my case, it was /boot/efi
After that, you’ll need to create new keys with sbctl by running:
sudo sbctl create-keys
Then, enroll the keys with:
sudo sbctl enroll-keys -m
Next, you’ll need to sign the necessary files. You can find out which files need to be signed by running:
sbctl verify
This command will show you which files require signing. You can sign them with:
sudo sbctl sign -s /efi/EFI/GRUB/grubx64.efi
After signing, verify once more with:
sudo sbctl verify
If everything looks good, reboot and enable Secure Boot. That’s it!
Also I’m new to Linux, this might need an edit, feel free to notify me if anything is wrong and needs an edit.
the other way is to suppress the policies
see https://news.itsfoss.com/windows-breaks-linux-dual-boot/
This topic was automatically closed 2 days after the last reply. New replies are no longer allowed.