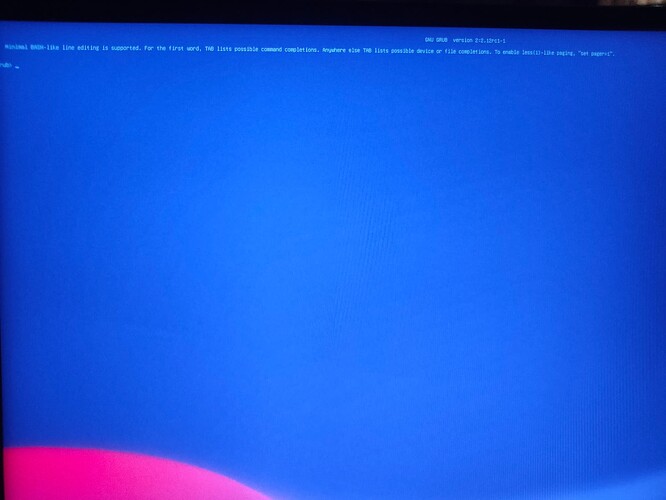
sorry, i understand.
Situation is not the best as i was about to start for a trip and i’m currently juggling on the move.
here the text
parted -l
Model: VendorCo ProductCode (scsi)
Disk /dev/sda: 15.7GB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Disk Flags:
Number Start End Size Type File system Flags
2 1933MB 2049MB 116MB primary fat16 esp
Model: WD PC SN735 SDBPNHH-1T00-1002 (nvme)
Disk /dev/nvme0n1: 1024GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Disk Flags:
Number Start End Size File system Name Flags
1 2097kB 1051MB 1049MB fat32 boot, esp
2 1051MB 1007GB 1006GB endeavouros
3 1007GB 1024GB 17.5GB
lsblk -f
NAME FSTYPE FSVER LABEL UUID FSAVAIL FSUSE% MOUNTPOINTS
loop0 squashfs 4.0 0 100% /run/archiso/airootfs
sda iso9660 Joliet Extension EOS_202305 2023-05-28-11-02-36-00
├─sda1 iso9660 Joliet Extension EOS_202305 2023-05-28-11-02-36-00 0 100% /run/archiso/bootmnt
└─sda2 vfat FAT16 ARCHISO_EFI 5770-579C
nvme0n1
├─nvme0n1p1 vfat FAT32 EB55-00CE 997.3M 0% /mnt/boot/efi
├─nvme0n1p2 crypto_LUKS 1 900288ed-a475-4001-bf41-54e379ea3fbd
│ └─luks-900288ed-a475-4001-bf41-54e379ea3fbd
│ btrfs endeavouros 93d5c885-df6e-439f-b0f3-6e6e4620cb3f 506.2G 46% /mnt/home/wolf/speedy
│ /mnt/home/.snapshots
│ /mnt/.snapshots
│ /mnt/mnt
│ /mnt/var/log
│ /mnt/var/cache
│ /mnt/home
│ /mnt
└─nvme0n1p3 crypto_LUKS 1 2e427ab1-0cad-4174-ab69-b379a0f2e1bc
└─luks-2e427ab1-0cad-4174-ab69-b379a0f2e1bc
swap 1 swap 83c1a51b-2f20-449e-81b7-c4a9268a6df3 [SWAP]
efibootmgr
BootCurrent: 0004
Timeout: 1 seconds
BootOrder: 0000,0003,0004,0002
Boot0000* endeavouros HD(1,GPT,3ed12d08-e58b-df40-a3ed-1f34693d67e1,0x1000,0x1f4000)/File(\EFI\endeavouros\grubx64.efi)
Boot0002* Windows Boot Manager VenHw(99e275e7-75a0-4b37-a2e6-c5385e6c00cb)57494e444f5753000100000088000000780000004200430044004f0042004a004500430054003d007b00390064006500610038003600320063002d0035006300640064002d0034006500370030002d0061006300630031002d006600330032006200330034003400640034003700390035007d00000000000100000010000000040000007fff0400
Boot0003* UEFI OS HD(1,GPT,3ed12d08-e58b-df40-a3ed-1f34693d67e1,0x1000,0x1f4000)/File(\EFI\BOOT\BOOTX64.EFI)0000424f
Boot0004* UEFI: VendorCoProductCode 2.00 PciRoot(0x0)/Pci(0x8,0x1)/Pci(0x0,0x4)/USB(0,0)/CDROM(1,0x399a80,0x37a98)0000424f
fstab
# /etc/fstab: static file system information.
#
# Use 'blkid' to print the universally unique identifier for a device; this may
# be used with UUID= as a more robust way to name devices that works even if
# disks are added and removed. See fstab(5).
#
# <file system> <mount point> <type> <options> <dump> <pass>
UUID=EB55-00CE /boot/efi vfat defaults,noatime 0 2
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd / btrfs subvol=/@,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /home btrfs subvol=/@home,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /var/cache btrfs subvol=/@cache,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /var/log btrfs subvol=/@log,defaults,noatime,compress=zstd 0 0
#/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /var btrfs subvol=/@var,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /mnt btrfs subvol=/@mnt,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /run/media btrfs subvol=/@media,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /.snapshots btrfs subvol=/@snapshots,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /home/.snapshots btrfs subvol=/@snapshots_home,defaults,noatime,compress=zstd 0 0
/dev/mapper/luks-2e427ab1-0cad-4174-ab69-b379a0f2e1bc swap swap defaults 0 0
tmpfs /tmp tmpfs defaults,noatime,mode=1777 0 0
# mount root
# /dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /mnt/.btrfs btrfs subvol=/,defaults,noatime,compress=zstd 0 0
# mount speedy if present
/dev/mapper/luks-900288ed-a475-4001-bf41-54e379ea3fbd /home/wolf/speedy btrfs subvol=/@speedy,defaults,noatime,compress=zstd 0 0
# UUID=B482-48E9 /mnt/speedy exfat defaults,nofail,x-systemd.device-timeout=10,x-systemd.automount,x-systemd.idle-timeout=10m,uid=wolf,gid=wolf 0 0
UUID=B482-48E9 /home/wolf/speedy exfat defaults,nofail,x-systemd.device-timeout=10,x-systemd.automount,x-systemd.idle-timeout=10m,uid=wolf,gid=wolf 0 0
crypttab
# /etc/crypttab: mappings for encrypted partitions.
#
# Each mapped device will be created in /dev/mapper, so your /etc/fstab
# should use the /dev/mapper/<name> paths for encrypted devices.
#
# See crypttab(5) for the supported syntax.
#
# NOTE: You need not list your root (/) partition here, but it must be set up
# beforehand by the initramfs (/etc/mkinitcpio.conf). The same applies
# to encrypted swap, which should be set up with mkinitcpio-openswap
# for resume support.
#
# <name> <device> <password> <options>
luks-900288ed-a475-4001-bf41-54e379ea3fbd UUID=900288ed-a475-4001-bf41-54e379ea3fbd /crypto_keyfile.bin luks
luks-2e427ab1-0cad-4174-ab69-b379a0f2e1bc UUID=2e427ab1-0cad-4174-ab69-b379a0f2e1bc /crypto_keyfile.bin luks
/etc/defult/grub
# GRUB boot loader configuration
GRUB_DEFAULT="EndeavourOS Linux, with Linux linux-zen"
GRUB_TIMEOUT="5"
GRUB_DISTRIBUTOR="EndeavourOS"
GRUB_CMDLINE_LINUX_DEFAULT="nowatchdog nvme_load=YES rd.luks.uuid=900288ed-a475-4001-bf41-54e379ea3fbd rd.luks.uuid=2e427ab1-0cad-4174-ab69-b379a0f2e1bc resume=/dev/mapper/luks-2e427ab1-0cad-4174-ab69-b379a0f2e1bc loglevel=7 lsm=landlock,lockdown,yama,integrity,apparmor,bpf audit=1"
#GRUB_CMDLINE_LINUX_DEFAULT="nowatchdog nvme_load=YES rd.luks.uuid=900288ed-a475-4001-bf41-54e379ea3fbd loglevel=7 lsm=landlock,lockdown,yama,integrity,apparmor,bpf audit=1"
GRUB_CMDLINE_LINUX=""
# Preload both GPT and MBR modules so that they are not missed
GRUB_PRELOAD_MODULES="part_gpt part_msdos"
# Uncomment to enable booting from LUKS encrypted devices
GRUB_ENABLE_CRYPTODISK="y"
# Set to 'countdown' or 'hidden' to change timeout behavior,
# press ESC key to display menu.
GRUB_TIMEOUT_STYLE="menu"
# Uncomment to use basic console
GRUB_TERMINAL_INPUT="console"
# Uncomment to disable graphical terminal
#GRUB_TERMINAL_OUTPUT="console"
# The resolution used on graphical terminal
# note that you can use only modes which your graphic card supports via VBE
# you can see them in real GRUB with the command `videoinfo'
GRUB_GFXMODE="auto"
# Uncomment to allow the kernel use the same resolution used by grub
GRUB_GFXPAYLOAD_LINUX="keep"
# Uncomment if you want GRUB to pass to the Linux kernel the old parameter
# format "root=/dev/xxx" instead of "root=/dev/disk/by-uuid/xxx"
#GRUB_DISABLE_LINUX_UUID="true"
# Uncomment to disable generation of recovery mode menu entries
GRUB_DISABLE_RECOVERY="true"
# Uncomment and set to the desired menu colors. Used by normal and wallpaper
# modes only. Entries specified as foreground/background.
#GRUB_COLOR_NORMAL="light-blue/black"
#GRUB_COLOR_HIGHLIGHT="light-cyan/blue"
# Uncomment one of them for the gfx desired, a image background or a gfxtheme
GRUB_BACKGROUND="/usr/share/endeavouros/splash.png"
#GRUB_THEME="/path/to/gfxtheme"
# Uncomment to get a beep at GRUB start
#GRUB_INIT_TUNE="480 440 1"
# Uncomment to make GRUB remember the last selection. This requires
# setting 'GRUB_DEFAULT=saved' above.
#GRUB_SAVEDEFAULT="false"
# Uncomment to disable submenus in boot menu
GRUB_DISABLE_SUBMENU="false"
# Probing for other operating systems is disabled for security reasons. Read
# documentation on GRUB_DISABLE_OS_PROBER, if still want to enable this
# functioality install os-prober and uncomment to detect and include other
# operating systems.
#GRUB_DISABLE_OS_PROBER="false"
the error
1 of 2 a start job is running for /dev/dis/by-uuid/93d5c885-439f-b0f3-6e6e4620cb3f
2 of 2 a start job is running for /dev/mapper/luks-2e427ab1-0cad-4174-ab69-b379a0f2e1bc
what happened
this morning i booted normally and was presented by grub cmdline instead of grub menu.
after numerous attempts, i successfully chrooted and reinstalled grub with install and mkconfig.
i noticed an /efi folder and deleted it, no idea why it was there
checking etckeeper, there are no differences in etc files from yesterday. ysterday it was booting perfectly
specifically, i searched closely for fstab, crypttab changes and nothing is there.
i did update the system which contained the kernel but there was no grub update
additionally, dracut rebuild was triggered.
this was on the 12 of august, the pc worked just fine on the 13th. only a daily autocommit was made by etckeeper with no changes
etckeeper git diff from aug 12th commit to todays show no relevant changes
this is EOS on btrfs on LUKS encryption.
question
why is systemd stuck on those 2 jobs when i can perfectly open the crypto partition from live usb and furthermore i can mount it and use mount -a when i chroot into it?
i’m a bit discomforted, was just about to go on a trip and looks like i’m fucked right on time
updated text @pebcak @joekamprad